Encryption/Decryption
This guide will cover the overview of encryption and decryption in the Integra ecosystem. It will also go over how examples of encryption/decryption are used in specific instances and also the ability to expand these usages into the blockchain authentication layer added on to existing applications.
Overview
There are two main types of encryption (also known as cryptography) symmetric (ok symmetric-key encryption) and public/private key encryption. The third topic this guide will cover is how both of these encryption methodologies are used in parallel to do large document and data encryption securely in the Integra ecosystem. The guide will dive deeper into both types of cryptography and how they are used in the Integra Ecosystem. They both have unique uses and are both important to understand the concepts before developing a blockchain authentication layer on top of an existing application.
In the decentralized world of blockchain and in the case of data transfer, data flowing between applications in a public network environment can flow across any number of nodes or networks and is viewable to anyone on the network. Cryptography ensures that even though these nodes can see the data, they cannot understand the data. This is where encryption becomes critical in data transfer and storing secure data, like the private key or other sensitive data.
Symmetric Encryption
Symmetric encryption is highly effective for large amounts of data, requires less processing power to produce the cipher and the overall algorithm is inexpensive in regards to cycles consumed. The preferred algorithm that is used in the Integra ecosystem for symmetric encryption is AES. AES works really well for large amounts of data in terms of processing power and speed. AES encryption uses the same secret key (passphrase) to both encrypt and decrypt the data. There are two values that can be used for AES encryption/cryptography, they are the key and IV. The key is always the passphrase that the user generates and can be used alone to encrypt and decrypt the information. The IV, also known as the initialization vector, provides randomization for the key along with the AES algorithm to produce more secure encryption. The IV is typically required to be random or pseudorandom, but sometimes an IV only needs to be unpredictable or unique. Below is the flow of symmetric encryption.
Figure 1: Symmetric-Key Encryption flow. The same key is used to encrypt and decrypt the document.
For encryption of the Integra Smart Identity Document private key, for any user on the Integra blockchain, AES with only a key-value (which is referred to as the passphrase) is used for the encryption of the private key. Other types of Integra documents are also encrypted in this manner and the AES key is auto-generated and sent to the user's phone while the document is sent to the email, this way the only way to decrypt the document is to have access to both the email and phone. When looking at the private key in an Integra Smart Identity Document, it looks like the following data in Figure 1, versus a typical RSA private key shown in Figure 2.
"private_key": "U2FsdGVkX1+vdHazY17UdN8L7Otk4wAs5+xhfgZT4qT4VR47adgeM1XsLgf/rinGfOV6ojhWdb1B2zvwavT/GgbZrfjNoSj4rLa8bhvK9TPuxy07BYLMGmNW20jYrvl8TwXc02+OFo9IkNLhgkz+4D1rZZW6a57RsojMNXAV8ZGLNPN/L+A/DlSYo6ZTrhrhFM49tPJpWPamFkntDMHMHsbRCkcZupoZs3B/Ir21l4eOjRrQIWjtPxEVTaSNyDDkgRfGI7xXoC6eAYmwy349r/aPq/Zlr4c77/Y0MRovFOWB7eqVOKYunWaGnnvpzBRF+/ICNM3boJ36mhUKi6N7u+K3K3oIbGjfbzM6BqwSpTYKf11P60CNavbWZIrUzw86umKLgH5VlqS3F90duPSPayuhxZJmsoYFV2k9Y5Qs0Knj3luC7CYla87c7KWKck5arGfp3X1qKnIg4wufV/+TpwkyJwu7Fmi3K8LZSPAbACorP1KAHqVUAUgzmx8fEZ/WxtIaYqhYRD5IxoxaZE5uwLpBj1sBN0ntqTOGeixG4SsZSxQTC4dNxRW0WkwW1yxfFunRFrfrJZEEKjH1+ZfJoXgttj+APEbs26nl5Vpjh1PcboYlip3dSyuPZP5j6mV6dS9idquNYxQdfJJnAbVxDr4TZUJhuwV/ac9NR1x5FD5Fhxso+s/Yj8GSaRALlqELZincFA40ifmwTVkOx35Erc+zJLbX4LaSQ7cMUc4bht95o35Ou4OcNPrAZQZ0zUJ4uFgRPx6Wh6sTFigy919vSIYkrLjoLMMGVzjJdPz0KjqxuCzb5Y9hdEkppWXX9VNiZn7Y3hXlfcbjwo9DrDAC2ef3+ly1hVkBf2I81nm3v5w1aPw/sVMA/o/ykTIR1Tqq3SgKlv2rgsfIMnTAuMxYr8bl8QIRkOYK+QdsWHYvb6B3yQ8c8q7ALB/9Gdt27/LOvQJPGuFdl2c08Bv7kJferRoJpTRslFxpIbV0VaY5Vwo0Ld/FAzxkrsH5mILk0hTqxEcURhrzBJ7+45vumb+j7eMNLLhd8Z0u9dGncXRjTjLZpzU++ue4B75h0Yw0yDIPeMsW2ikWVGwmExeRkC2B7q4SK0pGIPAFeoThSpOQiEd3dJGuj+7AudYfH39/YtvZ5ZqAAGJEvJNgA3eOakNYdZNRsjiKoUL2olpUD+a2D2vQy5+egAtbwLLliMoAYGjTBAl1NT/yMHKEqV0Ft9Z7hIYByqV2w0GdBIMAYH7JptXhi4lkwpz+KtS8IhyLFfFRw+J595sPDswXWu+bt+f6Yc/BSxeFmzoG9Y6tDaMruCNNaSdQE/Hfc+kzj80AAY0p0fQztkO9stG+5IhWyToTMsHWJObj6HszRErT4/DFY7j4hk92YwU2g9aR6EO7xP212wPG7S1QY2TY9EGC9wBdph/f42ExnHkzZeaM0HOUEMUYT0+i1pfN5WT7tzPRal9y/wzElRIIqv4HK/V2IZiKU0VhGs7e2XfaPcWKBLBwqrfzXbhIjX13IwXdDVQiQIoVEQ2IFhE5CSuiemjhiGkYG/qloc4qTy7kEdTeyoIRzRdbWJxm+5bTmfceirLkhFakHiaRWFDxFJmE9Yzk0voNaXtSfexe24ouZOENcsj8JEBaYYEHfqMGro4TbcviPMpYo/FpWLi10mzHmz3sqQYm/lO5ZTWclj+3mASaH0CzVXgrL18rSXzXHOWy7iNokYsTD/LyZE0b7N97NUTR2dymJqVTU1lNeErXUtyOH9VMVK5v/fZ8qQPMCZglCKRNp+dWbCINbddITzl/jYhPYiIegXWkqZYbEGV6nxbu+wFMbQDnrAhOcSu+smXph6Uq0XCEeUzrljFOc5z+N1MQzDiGp4Mtm+dli/xU9da6bAobXLWm4maJSYqZFDak0C7kz8ddMyySfRFeVuMb6ke31JfMvzqPvkftK8QrP3jhB34y3B2dhIpvMBK66bS52NwE5xcnbgYcloCw6n6kR9JMI/WxXrKUhvAFZM4N3Zznso+Dc78cK6crtBoBsnkVOjfCJUcpvF7Usz8B5BBPBdVITxLF8oJ09lyzqpSlRz+Tcw3aJdVAXiypFdSdP2/bnmTMH5iqjSWO6yLdjaBTD02LVUWTgapaLWMdb14IK0mbzB9b4o2OfzEKluMcKxTZyYhhrbqg4/QXPcnHOURem/zUqzab1F+GJ6iTtgyOcQ1k3JfGrj8eyVbDqO+g8XB7ojHJX8WAfTNbru1GAXrKw5nQcGbGr9RpOQ4iHzn2BhRYBwzUZOyKc3vMusvCUOZyNI6814gQI2QLRdNtQ6sPEwhYoolLCnDxWDZ9hUBHZk5YOPrGKc7ryooUSeZsWV258hX3v5XHbUj5n3eqw6lbGdlHeuvaBfoKr3g1N1z+k/nc6I5+2pzxgvmtHOzt3v/F6BT2bSdBaIRN6kMcIHNX7oUQhRrjzDEOw4lCOafMkImTvxTOft/lIqTKJCZLXiXMciTj4ViJzZ786qVqU0WKIvB/Z75NlJ6G0a0xfIOQ6H5CX0flLO4uYqCZihxgyo+VPi1t89M2MUfSAzVo7ZfSuLTQna72H+VSiR1itlBr9VqcC8tEqM3CwpMPY1I65GKgekZf4CM4Isbx5fg7wQrvAMsstnqnyVreXTNSeXVY+9NIO5j6HtR9ak5gdunJp/3XN06V/wBF7EuD5cXRSjv6t0DdzaJKCQLl1Td01sR8ruwJ6AfOX94sBKH4TWk8KT7/lif0uUBuJhUPmO0svjXBgDqi8oQBHXXkpqcnZ/nLvjlyZMfIdc3NyDz/OdVO/Lqx1gsdftxM+W/Jh+f3B56wOItm1pqVeOvIb1qfyTiyA2r0LJcoZQizE8WgPeX95v51T6n5LdqnW1IAGN057y8QMQW6Xdp9rUBRYOlykxzuZBonQyPQXMWREXPOpvJa/DnrnlaK5qsrXu9njAoGedfyDa1jcL0whVxkhKNwtqFCmz0QqvHEovwCP+0Otx/vfCGdTqlcEZhO4/lS4rc/nXNRfzQ3IQqPreGgEMxdfAS6wdeTCFEJ0Kee/gi+g2QmS+z9oowBTD6qpJiD2yrRMs5VVFRzKzZmF/iZKiXikBVZHD6LwQsPJ4J2T6L8IPxwmzs92s/yLtyre3FzZoeV99v0GM4qK1DfSrhT7Waq4h9SNIbHGbyjFdZ2rDK+hL8XWf4Z51Ep8slfHzFKH4mGe1al0t+V4nbPsAJQ7mnQDAtuB7nwJA5iTCzZXTUsBFW8OG4k/NleBuLvvUdP7ztVgsD5QFvCTaxkSkI4sHlZkIk83bDC5hoUQeOJiyI2In2GBosHR3KwVZZ/52UWeE7Z/sGV/peWd2UKYGXgjXCfYl/Zcp7qe31tzjmKnmPlKQWgABr82QTlAnPrhiU35Qe295eMK9EmWmpbwiLx5RbXaWg5/gMdrrEunZL2lWrVl2d1OPS4H50XRemoM8ZBrY5HgDn+rHwSjMytagEy0MZYpkan7dMFNTH7Y6WBrMAaZrF2xoLVi0450QCs0e5SppcCEzOb7GTzSHvsLj46WCKRBcobGJ3a6jJeVeyi2QNWKkKUn3bXJcEl7P/0SQ0Chl35/FpxoTNgjMaoJnCQHCauEoDLtAFJc9ky3/B2ObA8SDWsO5vQtOQiNDtPcPxv6oTu1cw5Lp91qjBd7IqCL3zWgKiDnY6OMl4r0jwW2nLndp7fVtK5W5rl5R6UEkuRMFl0DcODQFKc7fKPyKB/NXms6hcoA4qa0M9gGE3rcHfvvjSI/MfUKhZonz/TYmwfPi7Qo9mZ923xMNDvtOqM26fUInCa4pHiOuQ38tBgeSdf5D0IEhdZimuLqQlenDFbmHUXwf/dnqyza+P5PgEUy7x5y/zKbhvkvwCRknx4KLI2qu2XddiJRHUE/423b0ZdEg2xvKTEEvtIEx5Xxd/ezzLzQnDZF4PNCCp5nu52G28Cri29xAnRvkgH5AYt5X93UD10tYaEKRYdw+/kuoYz4cdZUAsG8fJsfLYfoB7M3BBPcpI6LUPBpDI2KzbuYSQizS4U1/tOSVPmc77IAmv3+j6KvZi2VUORLLjHBjiMeanvNdMpiDzd3PGqcA/yV7t5/G79lBwU67nHozs2QEbXQr18yeQICyEGZWnbu4isAcB2imCnUfZDOzGEsO2Ij6AP6er+Md4hJT29z8LrQRdsDEO3FYt3ejMvtM+A369vyNpxK/q6hJ1QAR6EjYn8COTlIIeNDkTS3jBK6jCLrXXON89OVM8wVp3juq5vmIEkF6jIUxEONQGx0AOF7L05ODrcMo7/sRNlV3CEwM131XVg8J+9VRJVVfVohTrNMoVoiFgSFCqmgHSgPadrPwMt"
Figure 1: AES encryption of RSA private key in Integra Smart Identity Document
"private_key": "-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQCqGKukO1De7zhZj6+H0qtjTkVxwTCpvKe4eCZ0FPqri0cb2JZfXJ/DgYSF6vUp
wmJG8wVQZKjeGcjDOL5UlsuusFncCzWBQ7RKNUSesmQRMSGkVb1/3j+skZ6UtW+5u09lHNsj6tQ5
1s1SPrCBkedbNf0Tp0GbMJDyR4e9T04ZZwIDAQABAoGAFijko56+qGyN8M0RVyaRAXz++xTqHBLh
3tx4VgMtrQ+WEgCjhoTwo23KMBAuJGSYnRmoBZM3lMfTKevIkAidPExvYCdm5dYq3XToLkkLv5L2
pIIVOFMDG+KESnAFV7l2c+cnzRMW0+b6f8mR1CJzZuxVLL6Q02fvLi55/mbSYxECQQDeAw6fiIQX
GukBI4eMZZt4nscy2o12KyYner3VpoeE+Np2q+Z3pvAMd/aNzQ/W9WaI+NRfcxUJrmfPwIGm63il
AkEAxCL5HQb2bQr4ByorcMWm/hEP2MZzROV73yF41hPsRC9m66KrheO9HPTJuo3/9s5p+sqGxOlF
L0NDt4SkosjgGwJAFklyR1uZ/wPJjj611cdBcztlPdqoxssQGnh85BzCj/u3WqBpE2vjvyyvyI5k
X6zk7S0ljKtt2jny2+00VsBerQJBAJGC1Mg5Oydo5NwD6BiROrPxGo2bpTbu/fhrT8ebHkTz2epl
U9VQQSQzY1oZMVX8i1m5WUTLPz2yLJIBQVdXqhMCQBGoiuSoSjafUhV7i1cEGpb88h5NBYZzWXGZ
37sJ5QsW+sJyoNde3xH8vdXhzU7eT82D6X/scw9RZz+/6rCJ4p0=
-----END RSA PRIVATE KEY-----"
Figure 2: RSA private key example. Note this RSA private key does not match the example from Figure 1
Later in this guide AES encryption with both Key and IV will be discussed in the section Encrypting Data below.
Public/Private Key Encryption
The recommended public key pair encryption algorithm for the Integra ecosystem, for small amounts of data, is RSA (Rivest-Shamir-Adelman). The important distinction between RSA and Symmetric encryption is that in public key pair encryption there is a public encryption key that is distinct from the decryption key. The downside of public key pair encryption is that it requires more calculations (using two large prime numbers and an auxiliary value) and is therefore a relatively slow algorithm. Due to the slowness of the algorithm, it is not appropriate to encrypt large amounts of data with this type of encryption. Below in figure 2 is how public key pair encryption works.
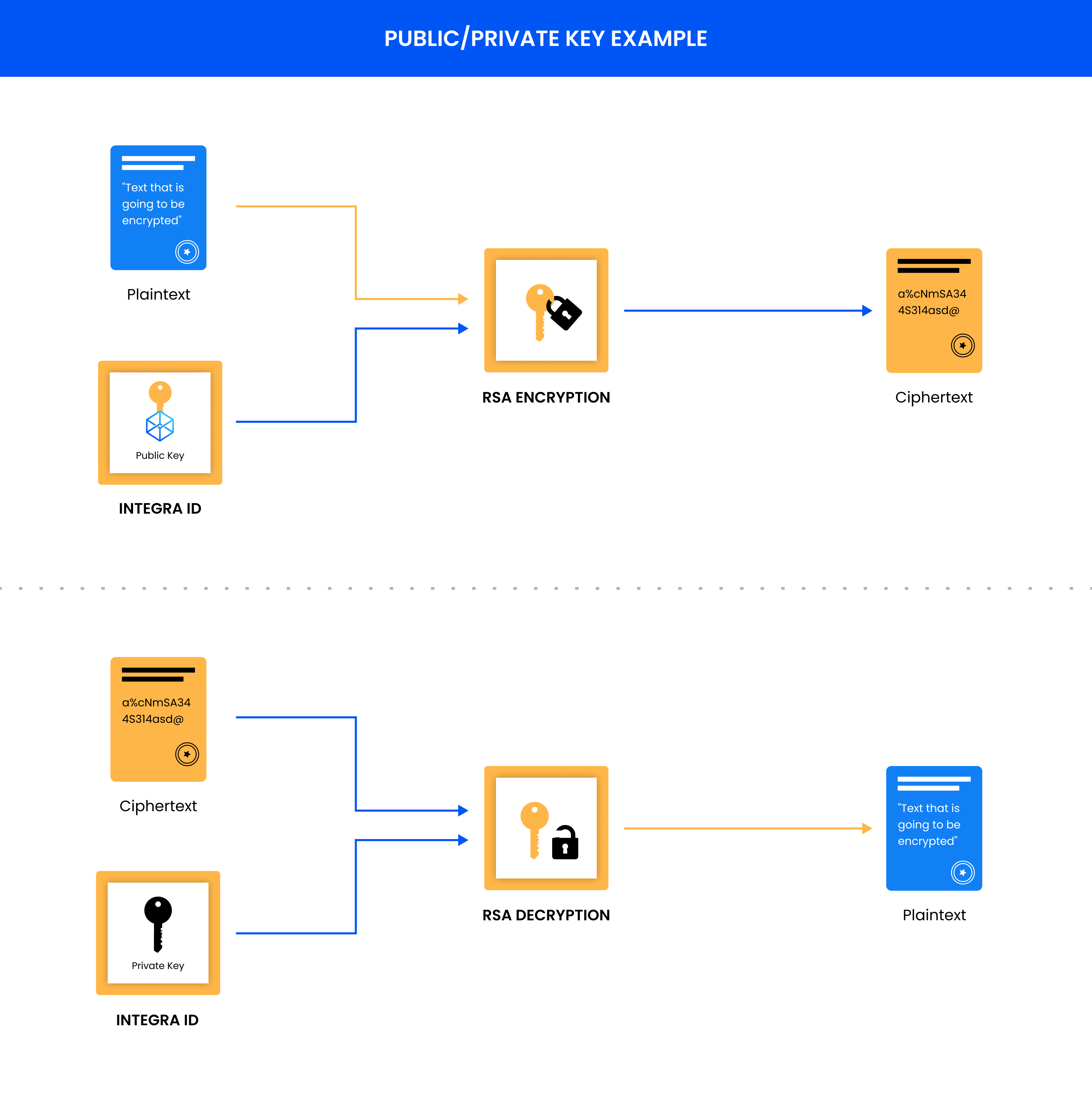
Figure 2: Public/Private Key Encryption and how it works for encrypting data between parties. The data is encrypted by the user's IntegraId/public key. The only way to decrypt the ciphertext is by having the private key that was created with the public key.
Public key pair encryption is very useful for encrypting data like messaging or codes that are used for Symmetric encryption. When it comes to encrypting an entire PDF file, this method carries too much overhead, and speed, to make it an acceptable solution. When encrypting messages or data, the first step is looking up the recipient's public key by using their IntegraId in order to look up their public key by using the KeyForOwner API call. The call takes in an IntegraId and returns an RSA public key. The format for the public key is shown below.
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEA+xGZ/wcz9ugFpP07Nspo6U17l0YhFiFpxxU4pTk3Lifz9R3zsIsu
ERwta7+fWIfxOo208ett/jhskiVodSEt3QBGh4XBipyWopKwZ93HHaDVZAALi/2A
+xTBtWdEo7XGUujKDvC2/aZKukfjpOiUI8AhLAfjmlcD/UZ1QPh0mHsglRNCmpCw
mwSXA9VNmhz+PiB+Dml4WWnKW/VHo2ujTXxq7+efMU4H2fny3Se3KYOsFPFGZ1TN
QSYlFuShWrHPtiLmUdPoP6CV2mML1tk+l7DIIqXrQhLUKDACeM5roMx0kLhUWB8P
+0uj1CNlNN4JRZlC7xFfqiMbFRU9Z4N6YwIDAQAB
-----END RSA PUBLIC KEY-----
The ciphertext that is created from RSA encryption can only be decrypted by the corresponding private key that was associated with the public key that encrypted the data. The communications using this type of encryption are suited for the public domain such as the Internet. This type of encryption only works if the private key remains in possession of the owner of the key. The possession of the private key is essential for the Integra ecosystem, this includes tokens, digital signatures, encrypted files, and other items, without the private key none of these others are valid. This works very much in the same way as the private key in every cryptocurrency.
Encrypting Data and Documents
The Integra ecosystem deals with large amounts of data in the form of documents so neither of these forms of encryption, on their own, work perfectly and or securely for the distributed network. Using the strengths of both encryption methodologies, Integra encrypts documents using both forms of encryption. Dealing with the large documents that are hashed on the network, AES encryption is used to encrypt the document itself, with a generated IV and key for the encryption of the document. The key and IV are then encrypted using the RSA encryption with the public key of the recipient. The public key encrypts this key and IV so only the holder of the corresponding private key will be able to decrypt the key and IV which will then allow the decryption of the original document using AES encryption. The speed and security of this method is ideal for the Integra ecosystem. Figure 3 below shows the metadata contained within an Integra Smart Encryption Document.
Figure 3: The image shows how the actual document's contents are encrypted using AES and the key/IV combo to generate the AES is encrypted with RSA encryption with the public key of the intended recipient.
Updated over 2 years ago
